Users and groups in UNIX
A group is a set of users to which a name is assigned. For example, the students’ group can belong to all the accounts of the students of a school or faculty.
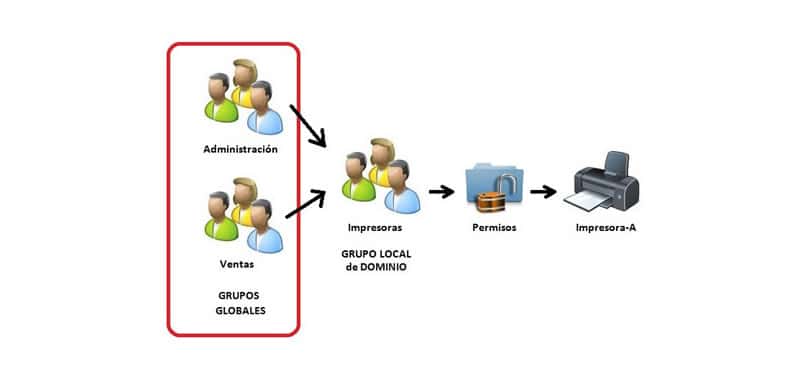
A group is a set of users to whom a name is assigned. For example, the students’ group can belong all the accounts of the students of a school or faculty.
A user can belong to several groups at the same time. For example, Joel belongs to the users, students and prn groups. The groups command will let you know which groups your account belongs to:
$groups
All users are part of at least one group, called the user's primary group.
As UNIX is multitasking, in general there will be many programs running at the same time.
To avoid interfering with each other, each program running, or process, is assigned to the user who launched it and the main group of it. It is then said that the process belongs to said user and said group.
In the same way all the files and programs of the system belong to a user and a group.
Thanks to this the administrator can limit the access of the users to the resources of the system. For example, you can make only users of the prn group use a printer.
The superuser
In every UNIX system there is a special account, called the superuser account, which the system administrator uses to manage it.
Using this account whose name is usually root, the administrator carries out the maintenance and administration of the system.
If you have your own UNIX computer (with Linux or Solaris) then you will have to act as administrator and put the system to work.
When the administrator enters the system to perform the administration tasks, he does so through an account that gives him maximum privileges.
For this reason, you should only use this account for these purposes, because an error can mean irreparable damage or loss of user data.
Information about users
UNIX systems have a database that contains the list of users that the system can use, that is, the list of system accounts.
For each account, the corresponding user's name is stored, along with their password and other data for internal use, in addition to certain personal information about the user.
This personal data constitutes the so-called GECOS field of the user database.
The user list is usually stored in the / etc. / passwd file. Some systems also use the / etc. / shadow file to save passwords separately, which is more secure.
In distributed systems the NIS system can be used so that multiple networked computers have access to the same user database.
As already indicated, along with the internal use information of the system, personal information about the user is also stored. This data can be consulted by any other user of the system by means of the finger command.
Just indicate the name of the user you want to investigate:
akus@akus-System-Product-Name:~$ finger akus
Login: akus Name: akus
Directory: /home/akus Shell: /bin/bash
On since Sun Jan 12 14:09 (CST) on tty7 from :0
1 hour 16 minutes idle
On since Sun Jan 12 14:32 (CST) on pts/0 from :0
50 minutes 48 seconds idle
On since Sun Jan 12 15:22 (CST) on pts/1 from :0
No mail.
No Plan.
It indicates its directory and its shell by default. If it is connected, it is indicated from when, and if not when it was the last time it was connected.
If the researched user takes more than a minute without typing anything in the terminal it is supposed to be inactive (in English idle) and it shows how long it has been like this. Then you can check if the user has an email or not and when was the last time you read it.
Remember that UNIX was developed in academic and research environments. In those days the project file stored information about the project on which the user was working.
The plan file was used to describe your current situation and your prospective work plans.
Currently the .plan and .project files are still used but with a different purpose. In general, people often use them to make public all kinds of information. Many users place quotes, jokes or drawings, but rarely a true plan or project.
Information accessible by finger can be modified using the chfn (change finger information) command. Just type in the order followed by enter:
akus@akus-System-Product-Name:~$ chfn
Contraseña:
Cambiando la información de usuario para akus
Introduzca el nuevo valor, o presione INTRO para el predeterminado
Nombre completo: akus
Número de habitación [3]:
Teléfono del trabajo [2262200]:
Teléfono de casa []:
In addition to the name you can enter other information, such as the room number and work and home telephones.
This information will be displayed with the rest of the data and the finger order.
In some systems, the chfn command is disabled, thus preventing public information from being modified.
Thanks to this through finger you can know the true identity of the user, and there is no possibility of it modifying it to pass itself off as another.
CITE ARTICLE
For homework, research, thesis, books, magazines, blogs or academic articles
APA Format Reference:
Delgado, Hugo. (2019).
Users and groups in UNIX.
Retrieved Nov 24, 2025, from
https://disenowebakus.net/en/users-groups-unix






